Staff wide IT announcements, infrastructure changes, scheduled maintenance and requests for information will always come directly from Tyler Rasmussen: [trasmussen@georgeandbell.com.](mailto:trasmussen@georgeandbell.com)
Please note, and [tyler.rasmussen\_a@georgeandbell.com](mailto:tyler.rasmussen_a@georgeandbell.com) are valid internal email addresses however you should never receive any communications from these email accounts.
### Partner & Managers
Partners and managers at George & Bell will only communicate company information **via their own work email address**. If you receive an email from a partner or manager that was not sent directly from their work account, please forward the message to IT for investigation.
The partner email addresses are:
| Brendan George |
|
| David Lee |
|
| Greg Heise |
|
| Jeremy Bell |
|
| Mackenzie Bell |
|
| Mike Greschner |
|
### Administration
You may receive email communications from the Administration department. Administration staff include:
Additionally, the administration staff use the following mailboxes for specific purposes:
| Info (public inquiries) | |
| Accounts Payable (for receiving invoices and receipts) | |
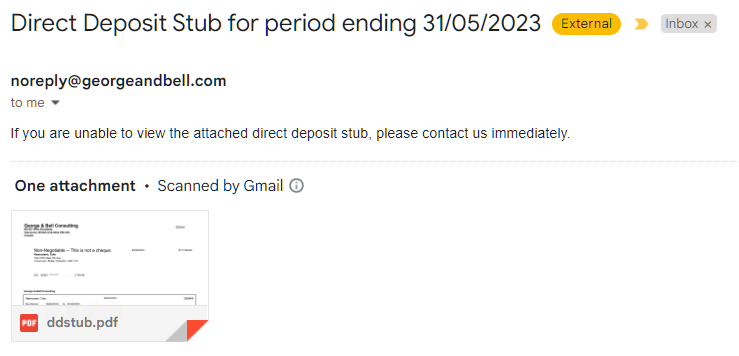
#### Paystubs
Paystubs are sent from the email account and will look as follows:
[](https://docs.georgeandbell.com/uploads/images/gallery/2023-05/direct-deposit-notification.png)
### Services
#### Scanned Documents
Documents scanned by Printer F within the copier room will be send via the email account. If you were not expecting a scanned document, do not open the attachment until confirmed that it's legitimate.
#### KnowBe4
Messages from KnowBe4 will arrive from [do-not-reply@knowbe4.com.](mailto:do-not-reply@knowbe4.com) Messages will typically consist of notification regarding enrollment or that a training campaign needs to be completed.
#### 1Password
Messages from 1Password will arrive from [no-reply@1password.com.](mailto:no-reply@1password.com) Messages will typically consist of invites onto its services or notification around managing your account.
#### Duo Mobile
Message from Duo Mobile will arrive from . Duo will rarely send out email messages. The only message to expect from Duo is the initial enrollment email.
#### Microsoft 365
Microsoft sends notifications from a variety of different email accounts, however consistently all accounts end in @microsoft.com. Please know Microsoft will **never** send you message asking you to:
- Check a voicemail message.
- Change a password.
#### LiquidFiles
Message from LiquidFiles will arrive from . LiquidFiles will only send messages relating to sending and/or receiving files.
### Phishing Attempt Response
If you receive an email or call from someone purporting to an IT technician and their phone number or email is not on this list please:
1. Hang up and refuse to speak with the caller. If via email, do not reply or open any links or attachments.
2. Notify your manager CC'ing Tom and Brendan.
3. Retain any information you may have on the call/email for future investigation.
# Phishing Information
# Example Phishing Message
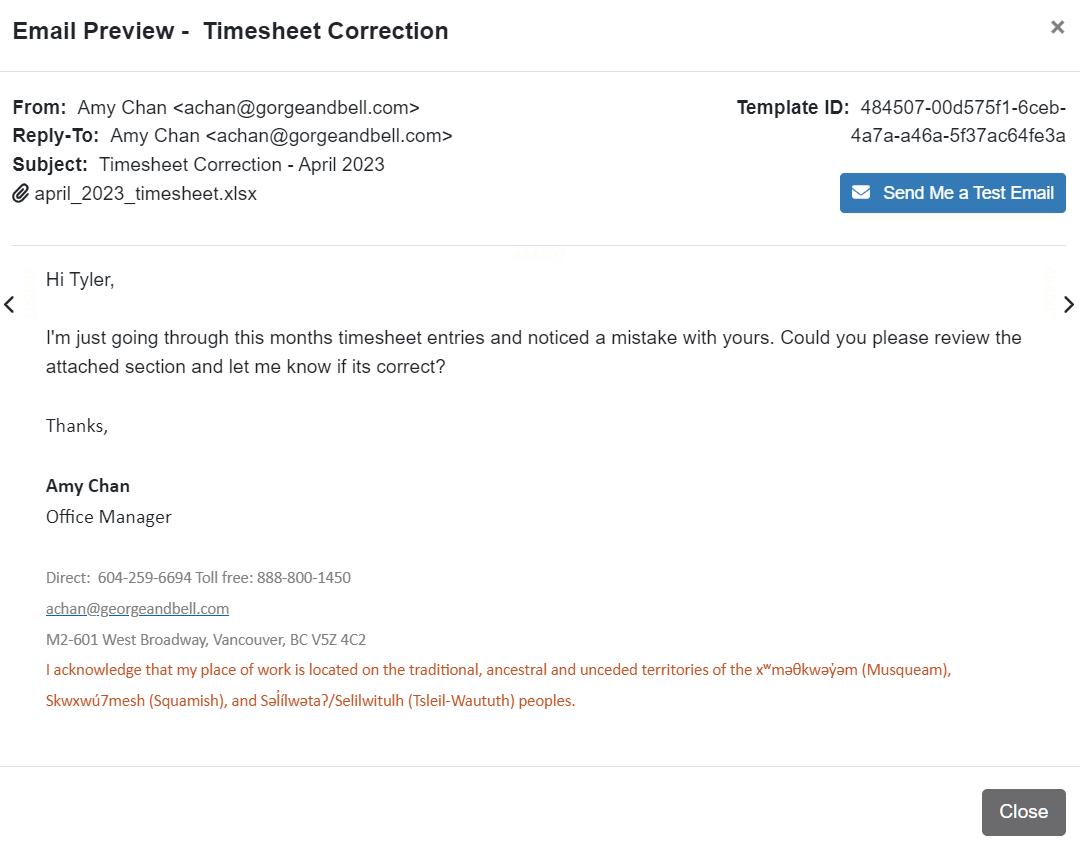
Below is an example phishing message.
[](https://docs.georgeandbell.com/uploads/images/gallery/2023-07/phishing-example-p1.png)
On first glance, the message looks completely legitimate. The email signature is correct, the email looks correct, the message is something that you would expect to receive and the attachment seems benign. There is really only one large give away and that was the sender email address. In it you can see that the “gorgeandbell.com” is missing the “e”. Another more subtle hint that may not give it away but is a potential red flag is the vagueness of the message. “Amy’s” request has no specific information regarding the request, other than to look at the attachment.
Here are some quick tips to avoid falling into the trap and opening a phishing such as the one above:
1. Always hover over and check the underlying link before clicking. Ensure the domain matches the message. For example a message from Microsoft should have a URL that ends in .microsoft.com.
2. Check and verify the sender address. Make sure it doesn't have any spelling mistakes.
3. Don’t open any attachments unless you’ve confirmed that the message is legitimate.
4. Keep a close eye on content of the message. Does the message sit right with you?
5. If you’re ever unsure, call the individual and have them verify the message.
# Phishing Tips
Phishing is the one of the most common and successfully methods of hacking into and breaching an organizations security. Here are a few tips on how to spot and prevent a successful phishing attack.
1. Do not click on any link or attachment you do not recognize nor expect.
2. Never provide sensitive information such as usernames, passwords, or credit card details over email.
3. Always check and validate the URL (hover over the link) before clicking through.
4. Always check the sender’s email address to confirm that its correct and not misspelled.
5. Many phishing emails contain spelling and grammar errors. While not a confirmation.
6. If unsure call the individual to verify the email is legitimate (if you know them).
#### Header Message
Our email service has been configured to always indicate when an email originates from an individual outside out company. If you see the following header at the top of an email and the email purports to be from from a George & Bell or SISS employee, its guaranteed to be fraudulent.
[](https://docs.georgeandbell.com/uploads/images/gallery/2023-07/phishing-tips-p2.png)
#### Company Notices
Written instructions from fellow George & Bell team members will generally be sent to you via email or Microsoft Teams. You will not receive instructions (particularly instructions to purchase goods/services or grant access to our server or confidential client information) through other services such as Facebook Messenger, WhatsApp etc.
If you do receive instructions via these mediums, you should confirm by speaking to the sender in person before acting on any instructions.
# Reading Email URLs
All email messages have their URLs modified so when clicked your directed to our spam filtering provider prior to being redirecting to the original URL. This allows our spam filtering provider to scan and verify the legitimately of the link before redirecting you to the site. If the site is found to be malicious, your attempt to access the site is blocked.
The downside of this service is that it makes verifying a link a little bit more difficult due to the added text the service adds to the URL. Below is information on how to read through this added information so you can manually check and verify the URL before proceeding.
Below is an example of what a link will look like within an email message.
To see this URL within an Office application, hover over a link for a few seconds.
```
https://url.avanan.click/v2/___https:/google.com/___.bXQtcHJvZC1hdi1jYS0yOmNh (shortened)
```
To read through this text and validate the original URL, look for the underscores within the link. The address between the underscores is always the original website. In this case, the original URL is:
```
https:/google.com/
```
If the address looks legitimate and safe, you know its safe to click and view.
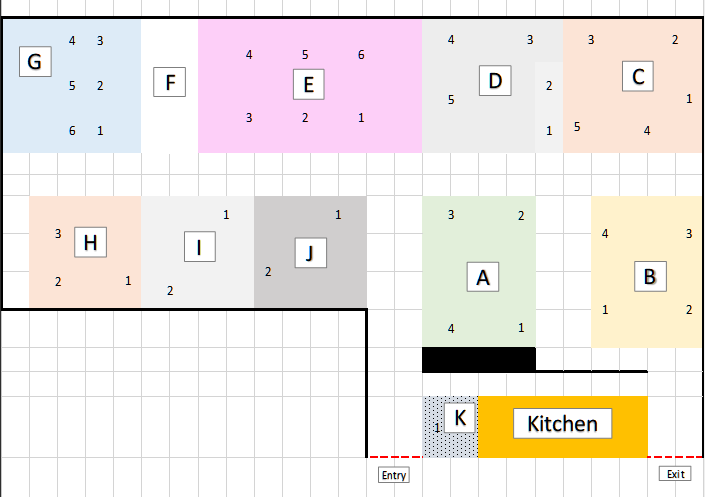
# Vancouver Office Seating Map
The following diagram outlines what number each desk within the office is labelled as. For example, the desk nearest the kitchen would be considered K1.
[](https://docs.georgeandbell.com/uploads/images/gallery/2023-05/vancouver-office-map.png)